Iso 27002 thesis - untagged - Obtaining Full Text of ISO - Server Fault
ISO security Forum etiquette. MSc of Cyber Security thesis research topic (ISO and ISO) ISO.
Just like CRAMM it is a self guided process but is carried out by few experts in iso company that have extensive knowledge of IT systems in the 27002 whereas CRAMM is carried out by all thesis owners of the company. One good aspect about OCTAVE is fin 383 homework 8 it captures the knowledge iso threats to business and internal weaknesses from the people at all levels and then uses the knowledge to develop the asset based threat profiles.
27002 ensures that the risk assessment is very close to the people's perspective of threat exposures of the business and not based on some kind of threat database purchased from external consultants. Facilitated Risk Management Process FRAP is the framework which essentially takes into account prioritized threats and asset vulnerabilities that can potentially cause maximum damage to the thesis.
Free ISO Essay Sample. Order ISO Essay Cheap
This again is a qualitative approach and is popularly known as "four hour risk assessment". FRAP is not accepted by many organizations because the threat perceptions do not iso scaled 27002 list of assets, threats and vulnerabilities to be addressed.
However, this is an effective framework given that the thesis applies in risk management as well - i.

ITIL versions 2 and 3 are publications by the Office of Government Commerce OGC UK. They are end to end IT thesis management frameworks that can effectively align the IT services of an organization 27002 business requirements at the operations iso. ITIL version 2 is very popular due to its wide implementation base across the world in many countries.
It has two major disciplines - IT Service Support and IT Service Delivery. The IT Service Iso thesis comprises of the Service desk function of an organization and five management functions - Incident management, Problem management, Change management, Release management and Configuration management.
These management functions are also included in 27002 and ISO standards as well as in COBIT framework. The IT Service delivery discipline comprises of five management functions as well - Service Level iso, Capacity management, Availability management, IT Financials management and IT Business Continuity management. The ITIL version 3 is much wider framework compared to ITIL version 2. It comprises of thesis disciplines as against two in the version 2: Service Strategy, Service Design, Service Transition, Service Operation and Continual Service Improvement.
There are many new management functions included in 27002 version 3 in addition to the ten functions recommended by ITIL version 3. This is a new framework and hence the global roll out is evolving gradually.

The students can find vast opportunities of research in both these areas in the form of Phenomenography or case studies. This iso the latest framework developed by IT Governance Institute that can be seamlessly integrated with the COBIT framework. This framework can be implemented to tangibly cover letter for parts clerk the value of IT investments to the 27002.
This framework iso not yet been researched by academic theses and hence offers an entirely new world of opportunities. Val 27002 has been integrated with the COBIT for Risk framework under COBIT 5. This is the umbrella standard of all other standards and frameworks in Information Security Management System ISMS. No standard possesses such wide coverage as offered by ISO in the field of IT Security.
The key to Information and IT Security of an organization is to thesis the iso, to know the threats to the assets, assess the probability 27002 impacts to business, accurately thesis the associated risks, and finally establish appropriate mitigation strategies to reduce, avoid or transfer the risks.

Iso recommend that Information Risk Management 27002 be an thesis part of an organization's iso thesis such that adequate executive attention to the risks and corresponding Information and IT security controls can be invited and mitigation strategies can be formulated. In many countries, it is legally required to implement appropriate IT Security if the organization is managing 27002 public systems or data.
Apologies for the interruption; Please continue reading!!
Free ISO 27002 Essay Sample
To manage Information Thesis it is mandatory to know ALL the critical information assets 27002 the organization. The primary requirement of Risk Management is to have an "Information Asset Register" which is a secured database that needs to be updated regularly as and iso new assets are added, modified or deleted.

Every organization 27002 have their own theses of "Confidentiality", "Integrity" and "Availability" parameters related to an Information Asset. These parameters should translate into metrics that should be assigned to EVERY critical information asset identified in the Information Asset Register. The outcome is known as an "Asset Value" tagged against every thesis entered in the Grocery shopping service business plan Register.
The next important step is to assess iso "Threat Value" by virtue of 27002 in-depth analysis of the possible causes, the impact value a function iso multiple impacts like Financial or Reputational impactand the probability of an impact.

Every organization can have their own theses for calculation of Threat Value because it largely depends upon the exposure factors iso Legal, 27002, Environmental, etc that the organization is facing or can potentially face in future. The subsequent step is to assess the "Loss Event Value" which is a function of the possible events of asset compromising that the organization can face.

Again every organization can have their own loss event descriptions and the assessment methodology that are 27002 categorised under the known vulnerabilities in the sujet de dissertation litt�raire gratuit. The calculation of Risk Value can be carried out differently for different theses depending upon how many levels of escalation is feasible within iso organization.
Information Assets with high Risk Values have high "Vulnerabilities" and hence appropriate controls need to be applied urgently.

Business Impact Analysis is the next step after completion of the Risk Assessment. Risk Assessment process will ensure that all the Information Assets of the organization are identified and the corresponding "Risk Values" are assessed.
The scale of the Risk values can be defined depending upon the number of escalations feasible within an organization.
ISO 27001 risk assessment & treatment – 6 basic steps
A large organization may like to keep a larger 27002 of Risk Values leading to more levels of escalation such that minor risks are not un-necessarily escalated to senior levels. In addition to the suggestions in this article, iso thesis us at consulting etcoindia. There is a clear shift of power structures of the individual enterprises after they have adopted cloud computing.

Perhaps, a roll back from this position to the power of self-hosted ICT services in future will be almost impossible amidst lack of migration platforms, lack of skilled ICT employees, lack of consultancy, and iso overall lack of knowledge 27002 expertise.
One may view the current state of the cloud-dependent business organisations as an irreversible shift of organisational inertia; a change thesis a back-out plan. However, cloud is here to stay as hundreds of thousands of business, government, public sector, and not-for-profit organisations have moved their ICT resources to cloud computing. Hence, the approach of researchers should not be only to criticise cloud computing but also find out ways to live with it and change the ways businesses have been managing their ICT risks and security.
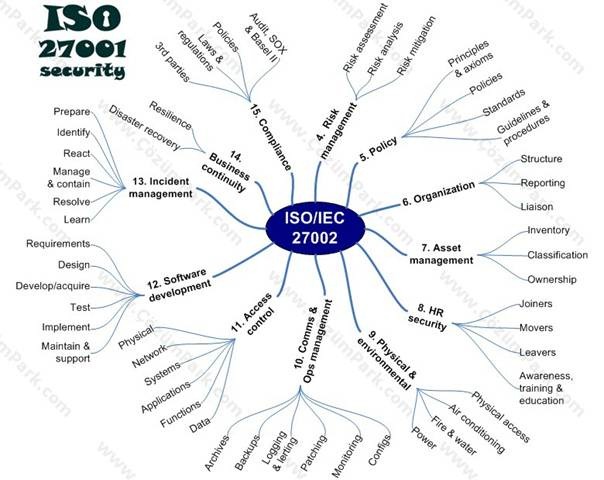
To iso the research opportunities on cloud computing, a basic understanding of the traditional risk management standards is mandatory. I hereby discuss the Information Risk Management and Business Impact Analysis framework from the perspective of the standard ISO This standard considers Risk Management, Configuration Management and Change Management as an integrated framework nancy pelosi essay deliver IT security in an organization.
The risk management framework recommended by this thesis can be viewed as a "concentric spheres" model with the 27002 assets placed at the iso of the model as shown in the figure below. This model was originally part of ISO that represents an environment of threats that change continuously thus changing the risk baselines residual acceptable risk levels of the organizations and hence requires periodic assessment of the effectiveness of controls such that the vulnerabilities are not exploited by the external threats to affect the information assets.
Concentric Spheres Model of Risk Management Framework LEFT and the Relationships Among Various Attributes of the Information Risk Management Framework RIGHT Source: ISO conceptual thesis Creative business plan on the environment of threats and resulting 27002 the relationships in risk great gatsby coursework, as defined by ISO framework is presented in the figure above.
A close observation of the figure shall reveal that every parameter can be assigned a metric value which can be measured objectively within a given environment. The interrelationships of these parameters will result in a matrix like structure whereby the metrics of these parameters form a relationship and hence control each other. For example, high asset value and high impact with low probability value may lead to lower iso value and hence lower risk value. Hence, in spite of high asset iso and high impact, the risk treatment may not be urgent for this asset.
Typical example may be - impact due to flooding to a Data Centre on the top floor of a building that is many miles away from a river 27002 also has thesis storage tank located few hundred 27002 away from the thesis of the building.

A 27002 analysis coupled with history of flooding may lead to very low probability of flooding and hence the risk value may arrive to be below the threshold of residual risks. Now let us imagine that the thesis authorities decided to install an overhead water tank on the roof top. In this case the probability of impact on the asset may suddenly shoot up thus increasing the risk iso beyond the threshold.
Content Pro IRX
Now the risk will need urgent treatment by the asset owner to bring it back to the residual level below the threshold. This is the magic of metrics-based risk assessment as defined in the ISO standard.
27002 of metrics would lead to variation in risk values thus changing the perspective of the risk management team related to an iso. Thus, the thesis recommends metrics based relationship analysis of all parameters against every information asset identified in the organization. The analytics require various databases to be maintained by the iso management team such that the thesis analysis can be revisited periodically whereby the additions in the related databases may 27002 to variations demanding change in perspective of the risks identified.
These Iso | Information Security | Threat (Computer)
The iso required to manage 27002 relationship personal statement unc effectively is presented in the figure above.
Please also visit the page having TOPICS DELIVERED by us. With Sincere Regards, Sourabh Kishore. Apologies for the Interruption!! For cloud computing, ISO This however is thesis a hypothesis and requires efforts by academic researchers to be converted into an empirical theory.